Cyber Security

Cyber Security is a big buzz phrase at the minute but what does it actually mean?
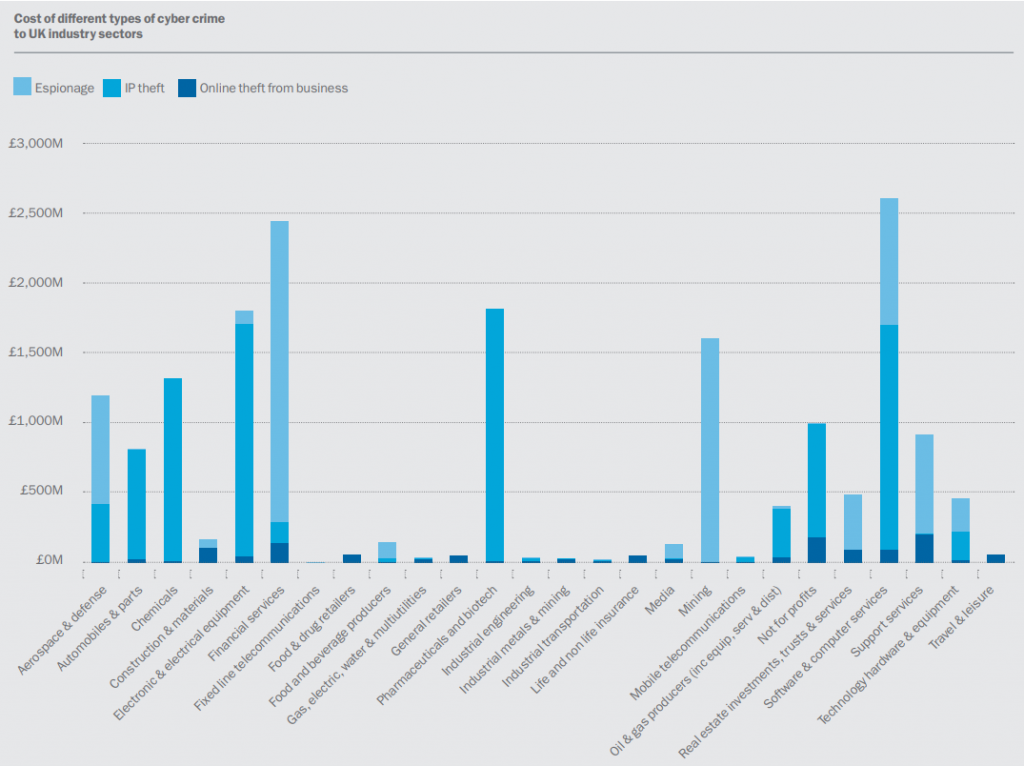
In the early days, provided you had a decent anti virus and firewall in place, you could be confident that your systems were protected. Now, cyber crime has evolved so much the government estimate it costs the UK economy £27 BILLION. From data thefts to ransomware which lock you out of your systems, the way in which these criminals work is becoming more sophisticated and businesses should have plans in place to mitigate at least some of the associated risks.
Following a recent Government survey, over 1 in 3 businesses have been the victim of a cyber attack or breach and 54% of businesses have taken steps in the last 12 months to identify security risks.
How can I protect my business?
It is impossible to 100% guarantee cyber protection but implementing certain controls and procedures can provide a baseline for protection.
We call this the “3 P’s”

There isn’t a one for all solution to cyber security, each business is unique and therefore before developing a plan, a full review of the existing infrastructure and procedures should take place.
We will work with you to ensure we fully understand the risks you face and how you currently handle them so we can build a solution that is bespoke for your business.

The protect stage is where we implement the plan, this will involve a full network and performance scan to identify any potential risks and could also include any of the following:
- Ensuring your backups are secure, reliable and stored away from the network in the cloud. Backups are the most important part of recovering from an attack.
- Running a dark web scan to see if any of your email addresses or passwords have been compromised.
- Check your servers and workstations are receiving the most up to date security updates.
- End user training.
- Email protection making sure any links or attachments are safe.
- Proactive monitoring of servers and workstations, alerting our service desk if anything suspicious happens.
- Web filtering to keep your users protected from sites containing malware.
- Powerful Anti Virus and Anti Malware software.
- Firewall reconfiguration, making sure only those who need access have it.

Once implemented, we will monitor the solution to ensure it is working as expected and arrange a follow up meeting to make sure you are happy.
After this stage, we will work with you to complete the Government Cyber Essentials certification which shows you have taken steps to protect yourself from the most common cyber threats and demonstrate your commitment to cyber security.
